
Table of Contents
Let me tell you how I was able to find my first "valid" interesting critical vulnerability on a Vulnerability Disclosure Programme. I hope you will learn something new from this write-up :)
var d_omain.tld = target.com
The Hunt Begins
In this non-technical post, I talk about CVSS 3.0 scoring system and CIA triad, how it works, and how to determine the severity of a vulnerability.
One day I was hunting on a Public Vulnerability Disclosure Programme that provides Hall Of Fame for valid submissions. It was a medium scoped target (*.domain.tld). So I started my private recon script for reconnaissance (I'm mentioning only 5% of it in this write-up).
Reconnaissance Phase
Commands (Taken from my private recon script):
Note: Some commands use double hyphens which may display differently.
subfinder -d domain.tld -all -o .temp/subfinder.txt
sublist3r -d domain.tld -e baidu,yahoo,google,bing,ask,netcraft,threatcrowd,ssl,passivedns -o .temp/sublist3r.txt
findomain -t domain.tld | sort -u | tee -a .temp/findomain.txt
assetfinder --subs-only domain.tld | tee -a .temp/assetfinder.txt
amass enum --passive -d domain.tld -o .temp/amass.txt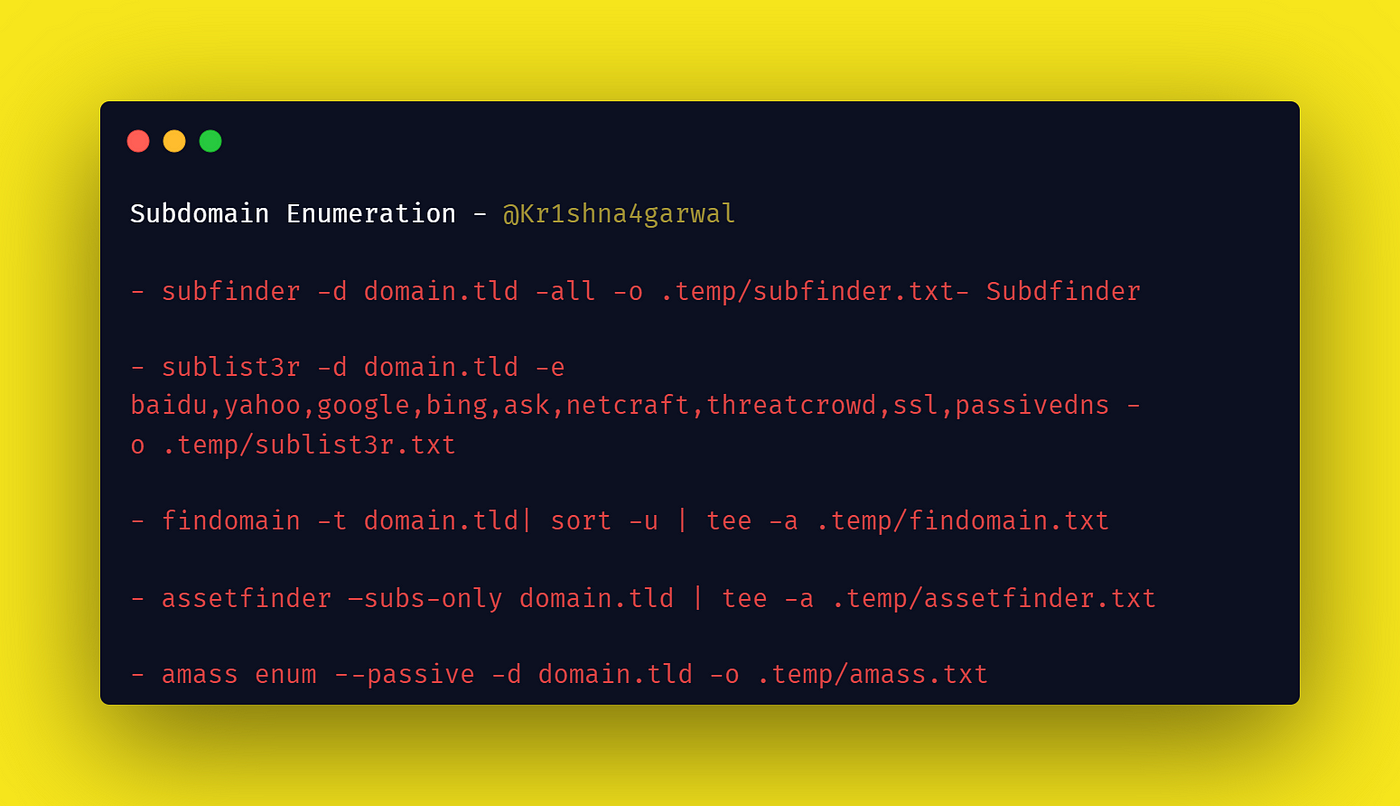
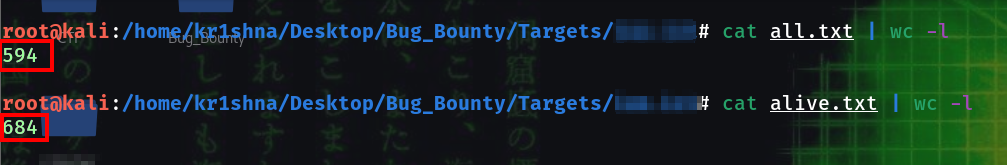
Got 594 subdomains.
After this I combined all the results and passed it to HTTPX:
cat .temp/*.txt | sort -u | grep -i domain.tld | tee -a all.txt
cat all.txt | httpx -silent -ports 80,443,3000,8080,8000,8081,8008,8888,8443,9000,9001,9090 | tee -a alive.txt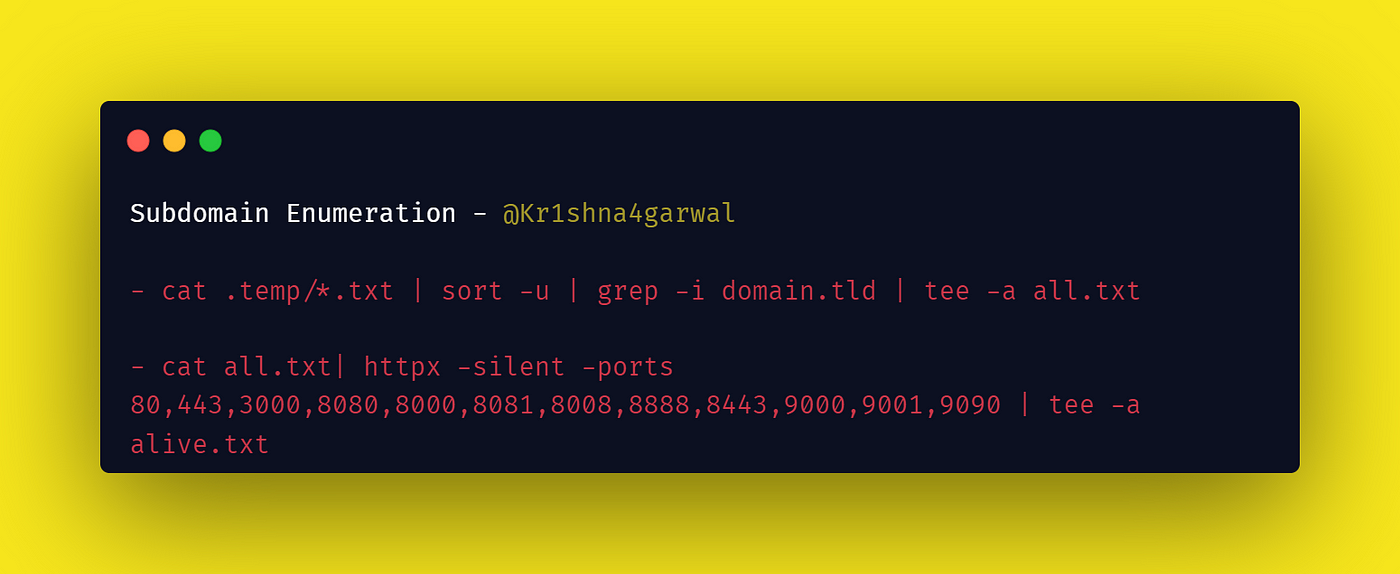
After HTTPX I got total 684 probed subdomains.
The Discovery
Now I started nuclei with my custom templates in background and moved all the subdomains to my Burp proxy configured browser (in 50 subdomains per window). While visiting each subdomain I found many 403 subdomains. For bypassing these forbidden subdomains I started 4-zero-3 in background, but no luck :(
Other 200 OK subdomains were feature-less (No signup, Login, etc) so I left these subdomains for future.
If you notice, I ran port scan with HTTPX and got some 8080, 8443, 9090 and 8081 ports open. So while checking the subdomains with ports (subdomains.domain.tld:<PORT>), I found one of the subdomains very interesting because it was running RavenDB on port 8080 with no authentication :)
What is RavenDB?
RavenDB is an open-source fully ACID document-oriented database written in C#, developed by Hibernating Rhinos Ltd. It is cross-platform, supported on Windows, Linux, and Mac OS. RavenDB stores data as JSON documents and can be deployed in distributed clusters with master-master replication.
In short: RavenDB is an open-source NoSQL Database.
The Critical Finding
So when I opened subdomain.domain.tld:8080 in my browser, I saw no authentication on RavenDB. I was able to change settings, dump full database, view system configurations, delete database (Obviously I don't have permission to do that).
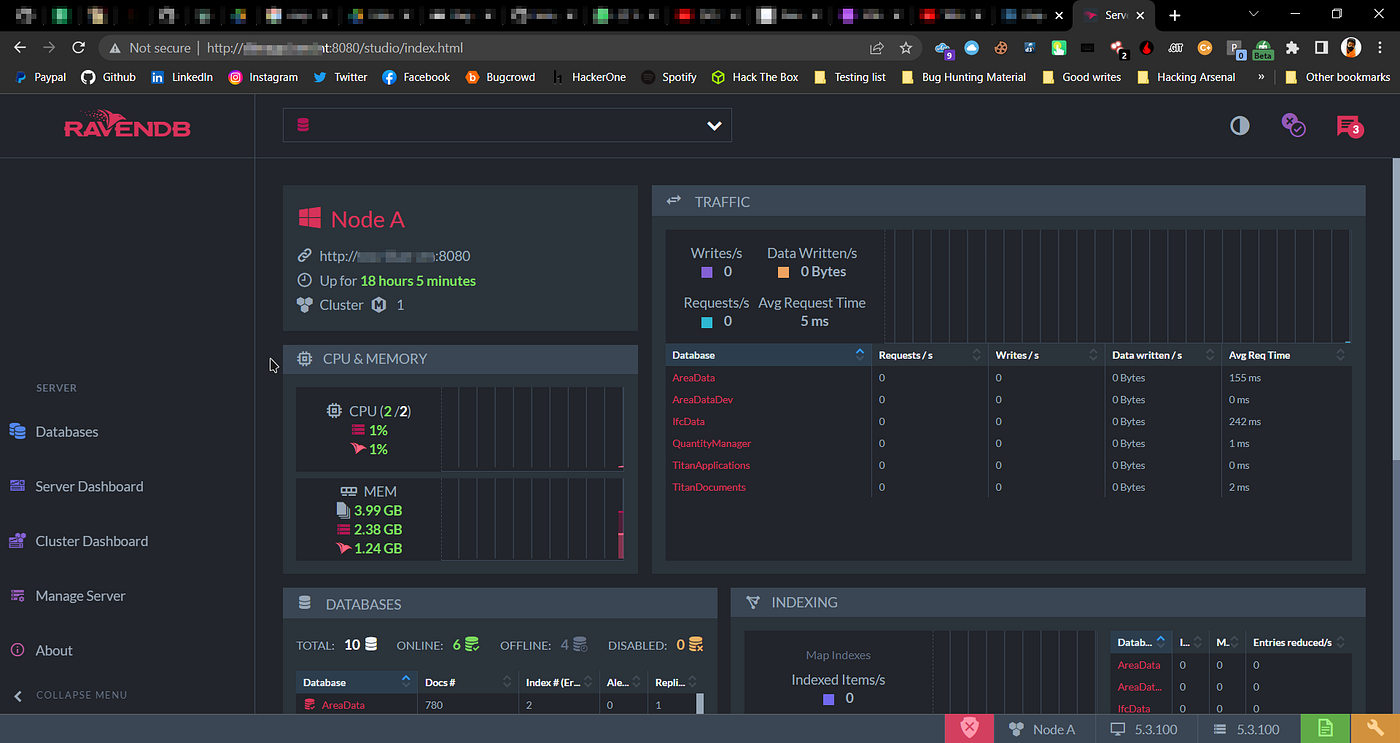 RavenDB Dashboard
RavenDB Dashboard
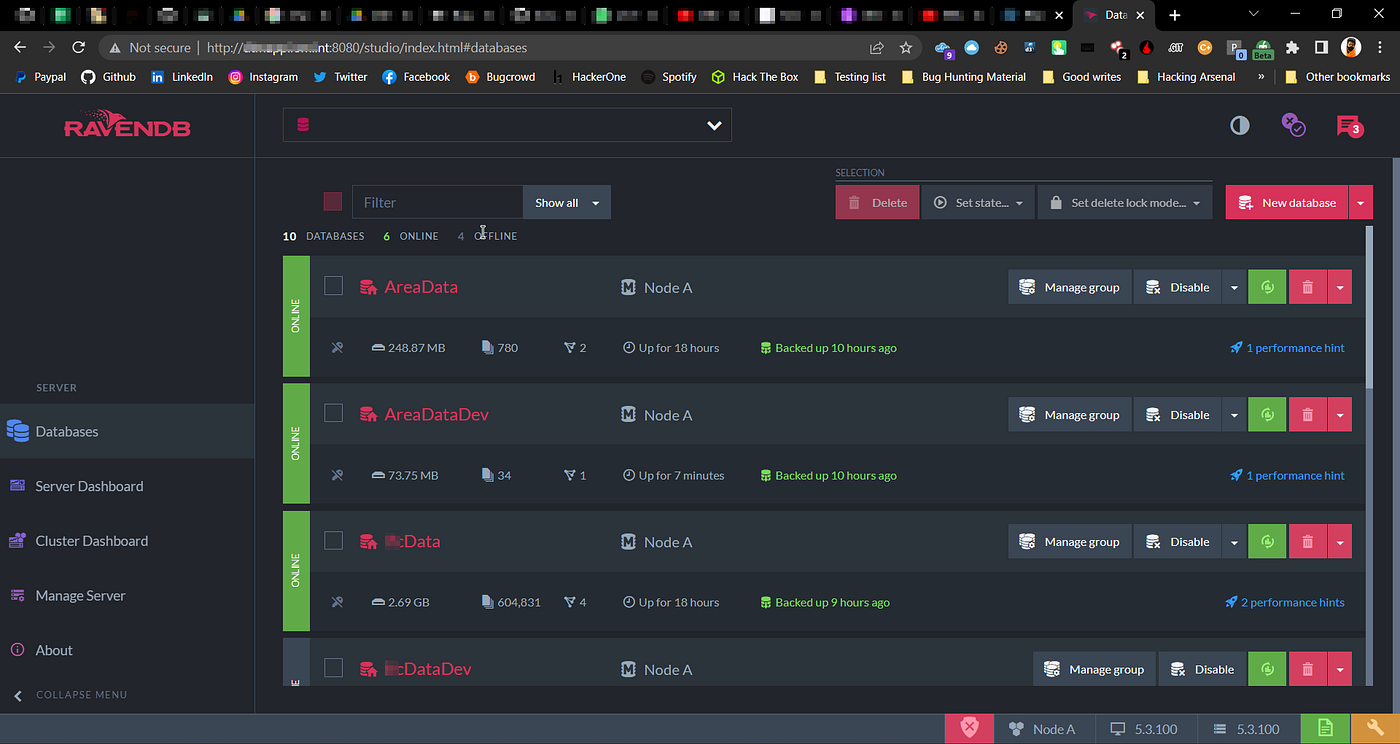 RavenDB Databases
RavenDB Databases
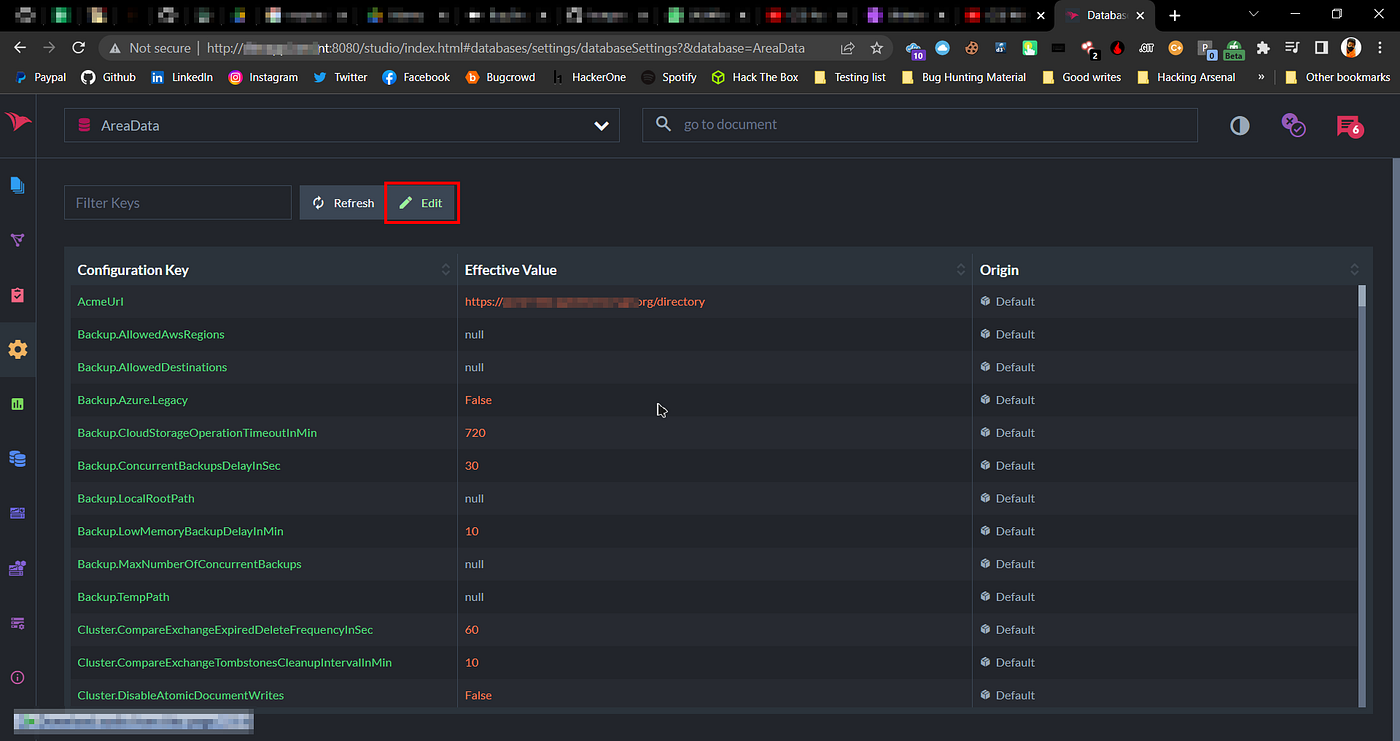 RavenDB Settings
RavenDB Settings
I quickly created a professional detailed report and sent it to the security team :)
Later I got some anonymous FTP, XSS and some common misconfigurations on the same target. It was enough for me, so I stopped hunting on that target.
Additional Findings
Update (12:22 AM, 19 July 2022):
Shodan Dork for finding RavenDB:
http.favicon.hash:442225173Pro Tips
Want to speed up your Nmap Scan? Use this command:
nmap 127.0.0.1 -sS -sV -Pn -n --max-rate 1000 --open -p 21 -oN Active_21.txtTip: Don't forget to scan the commonly open ports: 21, 22, 3000, 8080, 8000, 8081, 8008, 8888, 8443, 9000, 9001, 9090
Key Takeaways
- Comprehensive Reconnaissance: Using multiple subdomain enumeration tools increases your attack surface
- Port Scanning: Don't limit yourself to standard ports (80, 443) - many interesting services run on non-standard ports
- Database Exposures: Misconfigured databases are common and often contain sensitive data
- Automation: Background scanning while manual testing maximizes efficiency
Conclusion
This was my first valid critical bug - a simple yet impactful finding that taught me the importance of thorough reconnaissance and not overlooking non-standard ports. Sometimes the most critical vulnerabilities are hiding in plain sight.
Apologies for any grammatical mistakes.
DMs are always open for questions, help, collaboration, and suggestions :)
Connect with me:
Thanks for reading my write-up!
If you found this valuable, please share this with your infosec friends and community.
Keep hacking, keep learning!
Signing Off!
Table of Contents
Share
Share this article
More Posts
Explore more content from the blog
Honorable Hacking: How to Red Team Without Losing Your Soul
In this non-technical post, I talk about why red teaming doesn't have to turn you into the villain, discussed various non-technical aspects of responsible red teaming.
CIA triad and CVSS 3.0 | A complete guide
In this non-technical post, I talk about CVSS 3.0 scoring system and CIA triad, how it works, and how to determine the severity of a vulnerability.
Subscribe to Newsletter
Get notified about new posts and valuable content from me. No spam, unsubscribe anytime.

